Executive Summary
For a European company, owning only a .com domain while not controlling the corresponding .eu and .localCountry domains is not a minor oversight. It is a structural cybersecurity weakness that dramatically reduces attacker cost, increases attack success rates, and amplifies legal and reputational fallout.
This article explains — in concrete, operational terms — how exactly this makes an attacker’s life easier, why Greek and EU context matters, and why defensive domain ownership is one of the simplest, highest‑impact controls available.
1. Attackers Optimize for Ease, Not Sophistication
Most successful cyber attacks are not technically impressive.
They are cheap, scalable, and psychologically precise.
Missing domains give attackers:
- Free legitimacy
- Native language alignment
- Jurisdictional plausibility
- Zero need for technical exploits
If an attacker can choose between:
- hacking your infrastructure, or
- registering a domain you forgot to buy
They will always choose the second.
2. Domain Ownership Collapses or Expands Attacker Effort
From an attacker’s perspective, domain control determines:
- Whether email filtering applies
- Whether browser warnings appear
- Whether users hesitate
When you do not own company.gr or company.eu, the attacker:
- Bypasses your email security stack entirely
- Avoids impersonation detection
- Operates on a clean reputation slate
Your defenses never engage.
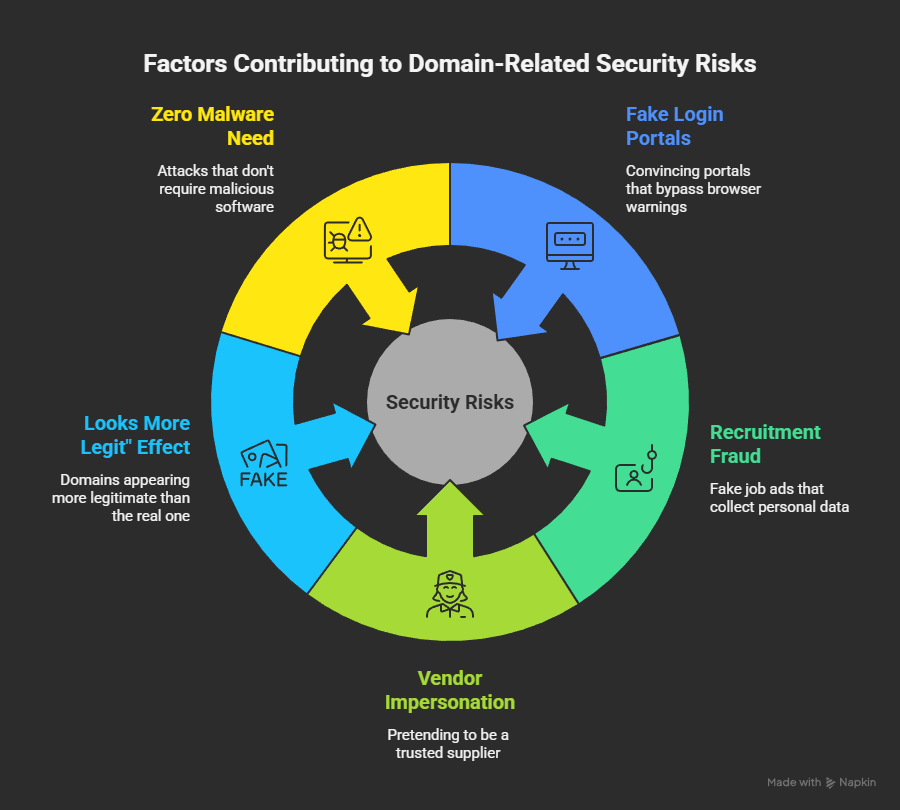
3. Concrete Ways Missing Domains Make Attacks Easier
3.1 Email That Automatically “Looks Right”
Compare:
No malware.
No spoofing.
No header manipulation.
Just a legitimate domain you failed to register.
Most recipients — including senior staff — will not question it.
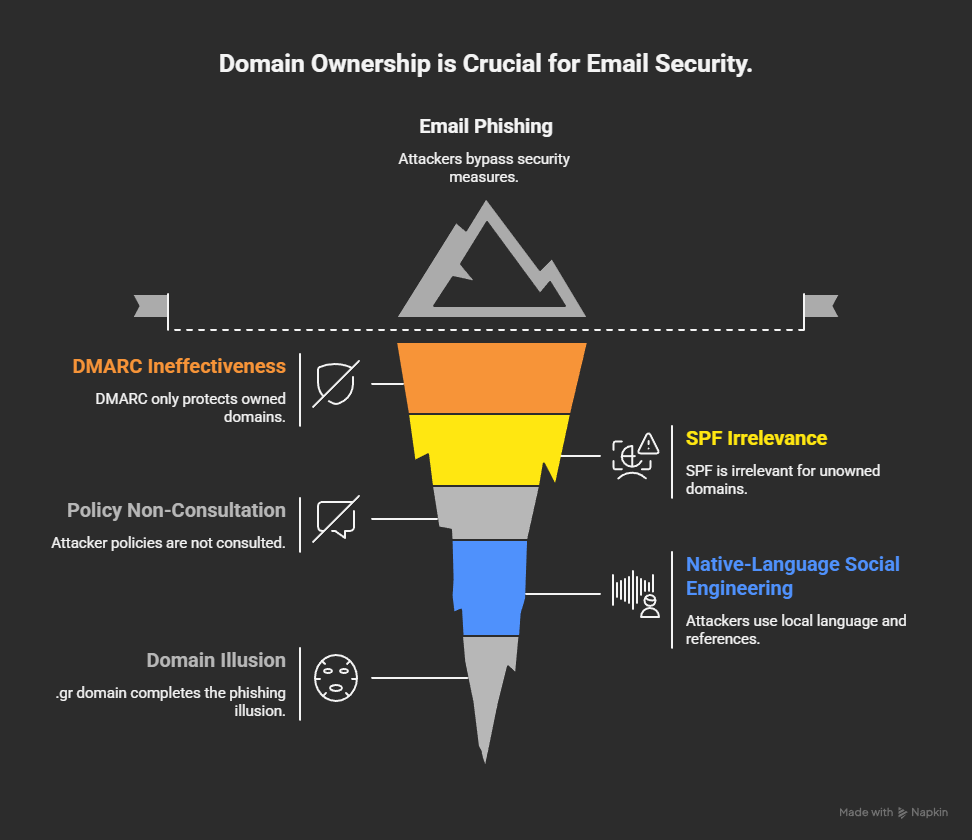
3.2 Bypassing DMARC, SPF, and DKIM Completely
Executives often believe:
“We have DMARC, so we are protected.”
That protection applies only to domains you own.
If an attacker sends email from company.eu:
- DMARC does not trigger
- SPF is irrelevant
- Your policies are not consulted
From a security standpoint, it is as if the attacker is a brand‑new, legitimate company.
3.3 Native-Language Social Engineering
Attackers targeting Greek companies routinely:
- Write emails in flawless Greek
- Reference local banks
- Use Greek legal or HR phrasing
A .gr domain completes the illusion.
Users do not think:
“Is this a phishing attack?”
They think:
“This is internal.”
3.4 Fake Login Portals Without Red Flags
Attackers can host convincing portals on:
- login.company.gr
- portal.company.eu
These domains:
- Do not trigger browser warnings
- Match expected URLs
- Appear more legitimate than shortened or foreign domains
Credential harvesting becomes trivial.
3.5 Recruitment Fraud at Scale
Greek companies are frequent targets of fake recruitment campaigns.
Attackers:
- Post job ads
- Link to careers.company.eu
- Collect CVs, IDs, and contact data
Victims associate the breach with your brand, not the attacker.
This converts a simple scam into a GDPR and reputational incident.
3.6 Vendor and Supplier Impersonation
With a controlled .gr or .eu domain, attackers:
- Request updated invoices
- Change IBAN details
- Reference real projects
Suppliers trust the domain.
Accounting processes fail silently.
3.7 “Looks More Legit Than the Real One” Effect
In some cases:
- company.com hosts English content
- company.gr hosts Greek-language phishing
For local users, the fake domain appears more authentic than the real one.
This inversion of trust is extremely dangerous.
3.8 Zero Need for Malware
The most damaging attacks:
- Use no malware
- Trigger no antivirus
- Leave no forensic artifacts
They rely entirely on trust and domain legitimacy.
Missing domains enable exactly this class of attack.
4. Why Legal and Regulatory Fallout Hits the Victim
After an incident:
- Customers blame the company
- Regulators investigate the company
- Media names the company
The attacker’s domain ownership is irrelevant to public perception.
You will be asked:
“Why was this domain not under your control?”
There is no defensible answer.
5. The Cost Curve Is Absurdly Asymmetric
| Action | Cost |
|---|---|
| Register .gr + .eu | Trivial |
| Monitor domains | Minimal |
| One successful fraud | High to catastrophic |
| Legal recovery | Expensive, slow, uncertain |
This is among the cheapest risk reductions available in cybersecurity.
6. Minimum Defensive Domain Strategy
A Greek company should, at minimum:
- Own:
- company.com
- company.gr
- company.eu
- Lock down:
- Redirect unused domains
- Disable mail by default
- Enforce DMARC reject
- Monitor:
- Lookalike registrations
- Early warning signals
Anything less is negligence, not oversight.
7. Final Thought
Cybersecurity failures are often framed as complex technical problems.
This one is not.
Failing to own your obvious domains hands attackers:
- Credibility
- Language alignment
- Jurisdictional trust
- Zero‑cost attack paths
In Greece, .gr and .eu domains are not optional.
They are part of your security perimeter.
If you do not claim them, someone else eventually will — and they will use them against you.
Appendix A — One-Page Defensive Domain Checklist (Executive-Ready)
This checklist is intentionally short. If any item is unchecked, the company is exposed.
1. Domain Ownership (Non-Negotiable)
- ☐ Own company.com (primary)
- ☐ Own company.eu
- ☐ Own company.gr
- ☐ Domains registered to the company legal entity, not individuals
- ☐ Registrar accounts protected with MFA
2. Domain Control & Lockdown
- ☐ All secondary domains either:
- ☐ 301-redirect to canonical site, or
- ☐ Parked with no active content
- ☐ No active web apps on defensive domains
- ☐ DNS change access restricted and logged
3. Email Safety Configuration
- ☐ No mailboxes enabled on defensive domains by default
- ☐ Explicit SPF records (even if mail is disabled)
- ☐ DKIM configured where applicable
- ☐ DMARC policy set to reject, not monitor
- ☐ DMARC reports actively reviewed
4. Lookalike & Abuse Monitoring
- ☐ Monitoring for newly registered lookalike domains
- ☐ Alerts routed to security or IT ownership
- ☐ Takedown or legal action playbook exists
5. Incident Readiness (Board-Level)
- ☐ Clear internal owner for domain risk (named role)
- ☐ Domain risk included in cyber risk register
- ☐ Cyber insurance explicitly covers fraud via impersonation domains
- ☐ Communications plan exists for fake-domain incidents
6. Audit & Governance Check
- ☐ Domain inventory reviewed annually
- ☐ Ownership verified after mergers, rebrands, or acquisitions
- ☐ Registrar recovery process tested
Board rule of thumb: If this checklist cannot be completed in under 30 minutes, domain risk is not under control.
What Auditors and Insurers Explicitly Look For
Auditors do not ask whether an attack was “sophisticated”. They assess foreseeability and preventive controls.
In domain-related incidents, reviewers typically examine:
- Existence of defensive registrations
Were obvious country and regional domains proactively registered? - Ownership and control evidence
Are domains owned by the legal entity, with documented access controls and MFA? - Preventive intent
Is there proof the company deliberately prevented misuse (parked domains, disabled mail)? - Policy alignment
Is domain risk referenced in the cyber risk register or ISMS scope? - Operational monitoring
Is there evidence of lookalike-domain monitoring and response capability? - Posture consistency
Does the company’s claimed security maturity match this basic hygiene?
Failure points are typically interpreted as:
- Lack of reasonable care
- Control gaps, not attacker brilliance
- Governance failure rather than technical failure
This assessment directly influences:
- Audit findings
- Insurance payout decisions
- Regulatory posture
- Board accountability